Which One of the Following is Most Important for a Continuous Review System
In a previous article on access rights review, we highlighted the differences between periodic and continuous access reviews and how to use each one. The conclusion was that the two approaches serve different purposes and should be seen as complementary. They do not replace each other. When used together, they are the most successful form of access review available.
When an organization is subject to one or more compliance regulations such as ISO 27002, NIST or Sarbanes Oxley (SOX), a periodic review of access rights is essential. Whether manual or automated, it is one of the cornerstones of the internal control process and allows an organization to demonstrate its access compliance to auditors.
Continuous access review is based on a hands-on approach. The hiring of a new employee, a job change within the company, the granting of additional access rights, security gaps and unusual permissions are all events that the continuous access rights review detects in order to trigger the necessary remediation and reduce security breaches which can lead to the theft or alteration of data.
For this second article, these explanations will be put into practice. Three use cases will illustrate the different ways to capitalize on the potential of both the periodic and continuous review of access rights to respond to the multiple issues found within organizations.
USE CASE #1: PERIODIC ACCESS REVIEWS AND SOX COMPLIANCE
The organization in this use case is a financial institution that manages more than 50,000 identities. Its problem is ensuring the compliance of its accesses and being able to demonstrate this to auditors.
The Periodic Review Applied to Financial Systems
Sarbanes-Oxley regulations require organizations to regularly review access rights to applications that allow the manipulation of financial data and similar resources. This is particularly important as a way of guaranteeing that they are being properly managed so as to avoid the risk of fraud. To do this, it is necessary to verify that a certain number of constraints within the financial systems. In the United States, auditors are the ones who must certify that these constraints are in place, and in Europe, statutory auditors are required to do the same.
In this specific case, the organization must meet a compliance objective and prove this compliance by showing the control processes and the correct management of access rights within the financial scope. To meet these requirements, a quarterly or annual review of access rights is best.
Objective : Validate User Authorizations
Every few months, team leaders are required to list and validate all authorizations. This involves checking several things, with a particular focus on:
- business applications related to financial transactions as well as their underlying infrastructures, and
- SOX-sensitive permissions, or permissions that have "write" access to data or that can modify a configuration system.
The next step is to process all remediation requests that result from these validations. In the case of this organization, any revocation decision triggers a service ticket (ITSM).
The periodic review of access rights is used here to demonstrate the compliance of the granted authorizations. The auditors will comment once they are sure that all the necessary controls have been carried out in a timely manner, and that a certain level of completeness has been reached. This is very important, and even more important than the validation of the data itself. For example, if all the data is validated without being reviewed first, the auditor will not take into consideration the fact there are no revocations, his objective being only to ensure that the control processes themselves have been performed.
Period Access Reviews with Tight Deadlines
In this example, the organization has opted for quarterly access rights reviews, which are broken down into the following three steps.
- The campaign is prepared, and the scope of the review is defined, all of which takes a total of two to three days.
- The lists created during the scope definition phase are distributed to the reviewers through the workflow engine. In this case, there are a total of 1,000 reviewers who have exactly 30 days to complete the review.
- The results are then consolidated, and remediation actions are initiated during the following two weeks to solve the problems identified during the review.
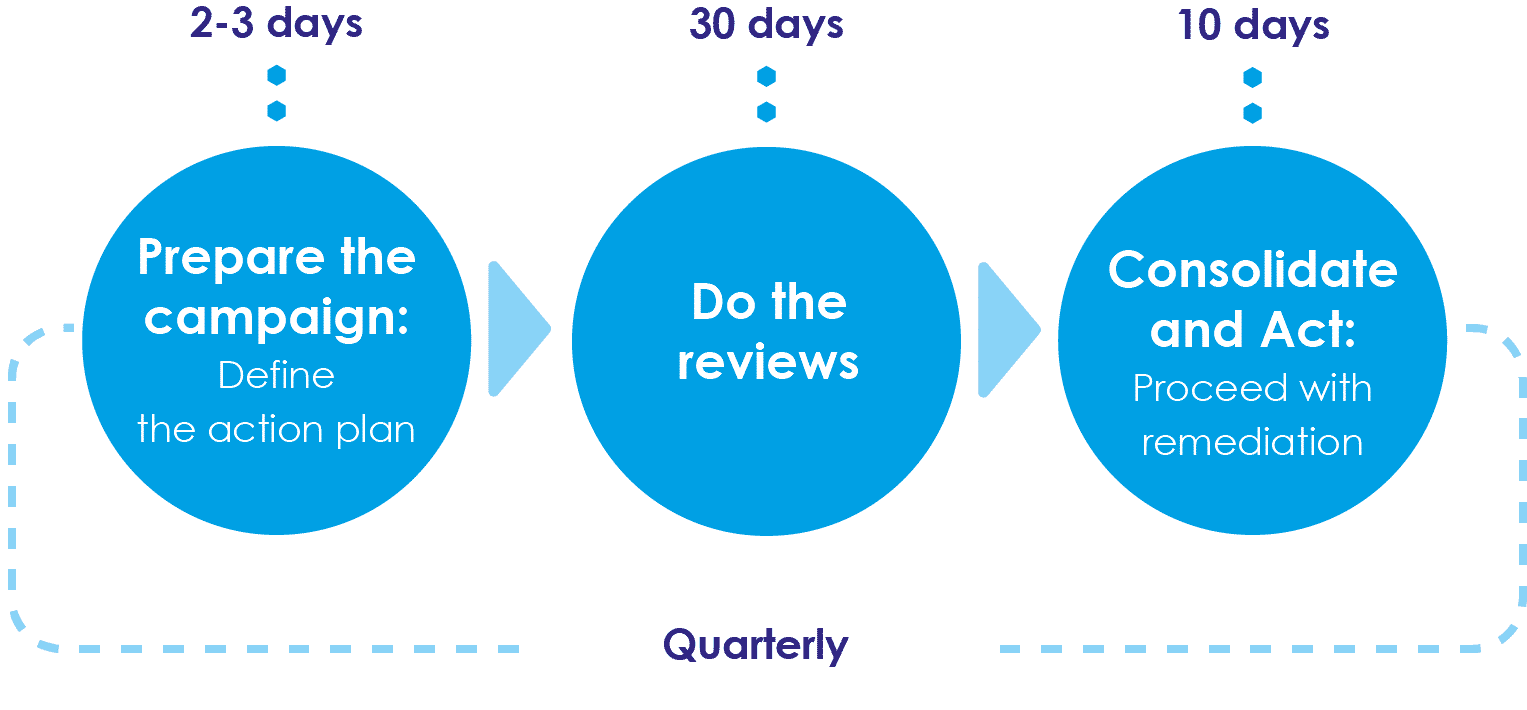
Since the objective of the periodic review of access rights is to ensure compliance, it is essential to respect the deadlines. Depending on the situation, it might be preferable to consider automatically revoking the accesses that have not been reviewed within the given time frame. In fact, it is difficult to demonstrate the compliance of one's accesses when only some of them have been reviewed.
Compliance requires a complete review of the targeted scope, which is an integral part of the periodic access review process.
NOTE: During these three steps, Brainwave's solution helps the reviewer with the functionalities listed below.
- Because read-only access is not considered sensitive within the context of Sarbanes-Oxley compliance, it can be pre-approved by default. Within the tool, the reviewer can automatically detect all accesses approved by default.
- Certain problems, such as control deviation, can be highlighted and suggested actions offered to the reviewer.
- Unusual or atypical situations that lead to revocation can be handled automatically without the intervention of the reviewer.
- Access to previous reviews that provide historical content can help with current decision-making tasks.
USE CASE #2: USING CONTINUOUS RIGHTS REVIEW TO TAG TECHNICAL ACCOUNTS
This second use case is based on the practice of reviewing access rights within an international group. This software publisher has several hundreds of thousands of identities and needs to determine all existing technical accounts to ensure that they are assigned to the right people.
Better Identification of Technical Accounts for Relevant Allocations
Within each organization, there exist several types of accounts, including:
- nominative accounts assigned to individuals who have exclusive use of them, and
- shared accounts to which access is generally granted to a group of employees.
In addition to named accounts, many employees have access to technical, service or administrative accounts. Just like with named accounts, it is important to keep track of who has access and is responsible for them to be sure that the access granted is always relevant.
In this use case, the software publisher has several various and outdated Unix-Linux system accounts, within which many local accounts have been created.
Taking this into consideration, access reviews have two main objectives:
- to list all system and technical accounts and to ensure that each one is assigned to the right person, namely, the system administrators and users who are responsible for these accounts from a compliance perspective, and
- to eliminate any ambiguity in the identification and use of accounts due the fact that the naming conventions for these accounts may not have been applied.
Choosing Continuous Access Rights Reviews for Address Identified Issues
In this specific case, the implementation of continuous access rights reviews is done after, but in conjunction with, the periodic review of access rights. This complimentary approach makes it possible to process several tens of thousands of accounts according to a flow logic that helps pinpoint related incidents.
The continuous access rights review is like the queue of a ticketing system, as seen below.
- More than 10,000 unknown accounts whose history has been lost or is uncertain are put a queue.
- Each account is reviewed to determine ownership, usage, proper assignment and validity.
- Depending on the answers obtained, a remediation process will be triggered to correct the information and the details of the account, or, if necessary, to revoke it if it is no longer in use. The progress is measured using key performance indicators and traditional flow measurements, such as the number of accounts processed per week or the number of accounts remaining to be processed.
Once these accounts have been tagged and categorized, they can be reintegrated into the compliance process via the periodic access rights review. The objective of this review will be to ensure that these accounts are still pertinent with regards to the organization's compliance framework.
USE CASE #3: FROM MICRO-CERTIFICATION TO THE CONTINUOUS RIGHTS REVIEW
This last use case is based on an organization's need to do reviews on a large volume of data.
The Principles of Micro-Certification
Micro-certification is part of a "get clean, stay clean" principle which means that once a situation of global control has been reached, micro-certification can be used to maintain an optimal level of data quality. This process makes it possible to work only on changes and security gaps. As part of compliance efficiency, the objective is to reduce risks by increasing the review frequency while, at the same time, reducing the workload.
To be effective, micro-certifications:
- must be frequent, of short duration and focus on changes,
- must be perfect in their execution to avoid backlog accumulation, and
- are most effective when performed within a mature organization.
Micro-certification can be considered a highly optimized periodic certification with continual frequency that meets compliance objectives. When dealing with sensitive resources, it is advantageous to do monthly micro-certifications between periodic reviews, as these will focus only on any changes that may have occurred in the meantime. By combining micro-certifications with periodic reviews, compliance and risk-reduction objectives are efficiently met.
Periodic vs. Continuous Access Rights Review: When to use a combined approach?
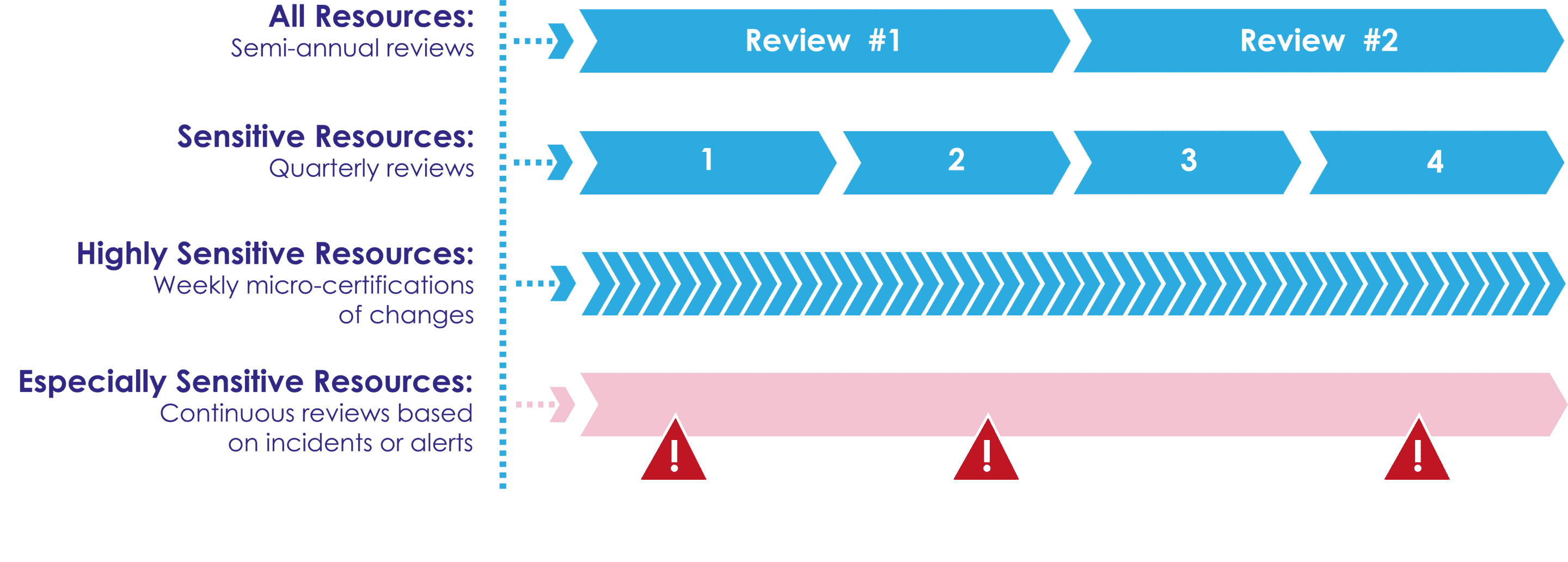
The combined methodology described here was deployed by a large financial institution with a level of maturity that is relatively unusual in the market. The use of different types of reviews is played out according to the level of sensitivity of the resources:
- All resources are subject to a semi-annual periodic review.
- Sensitive resources with a specific level of confidentiality are reviewed on a quarterly basis.
- The highly sensitive resources are subject to a weekly micro-certification process, the objective being to identify changes to avoid security breaches. In this example, this refers to administrative groups giving access to the organization's core business systems.
At the same time, a continuous access rights review is also performed. This consists of reviewing incidents such as deviations on high-risk controls, for example. Each incident is subject to an alert that can occur at any time, in which case it becomes necessary to take immediate action.
By using this method, the organization successfully handles the following challenges.
- The compliance objective is met through the implementation of periodic reviews complemented by the micro-certification process, optimizing the overall review process.
- Risk management is ensured with the help of continuous access rights review in addition to an effective alert system.
It is interesting to note how complementary the different review approaches are in terms of regaining control of accesses. While periodic reviews and micro-certification will demonstrate access compliance to auditors, continuous access reviews will contribute to considerable risk reduction. All of this is based on an analysis of all the organization's resources.
Any organization looking to protect its resources and infrastructure from security risk and meet compliance objectives should carefully consider the best review methodology prior to putting it in place. As demonstrated by these case studies, one approach is no more secure or effective than another. Risk mitigation and compliance is all about developing the right review strategy and may include, as shown here, a combination of several review practices for the best and most effective results.

Source: https://www.brainwavegrc.com/periodic-continuous-user-access-review/
0 Response to "Which One of the Following is Most Important for a Continuous Review System"
Post a Comment